Drug dealers use social media, surface and dark websites to sell illegal narcotics. Learn how OSINT techniques and Silo for Research can help crack the case.
The rise in social media since the early 2000s has led to drug dealers using various social media platforms to sell illegal narcotics on the open web. Investigators need a safe and anonymous browsing and research framework that allows them to investigate social media drug dealers without the risk of being identified or infecting their endpoint with malicious web code. This workflow will cover how Silo for Research, a purpose-built managed attribution platform, can be utilized to identify and investigate social media drug dealers anonymously.
How can OSINT be leveraged to fight drug traffickers?
OSINT can be critical in combating drug trade activities by providing actionable intelligence to law enforcement agencies. Here are the main ways in which OSINT can be utilized to fight this illegal trade:
Tracking drug traffickers
OSINT can be used to collect intelligence about individuals and organizations behind the drug trade. For instance, we can track suspected drug traffickers via social media networks to discover their associates, where they have been and to discover delivery routes. Drug dealers use the internet extensively, including internet messaging applications (e.g., WhatsApp, Telegram and Signal) to communicate and to plan future operations.
Tracking financial transactions
OSINT can help track monetary transactions between drug traders, discover money laundering activities and drug dealers' assets worldwide. For example, in the financial investigation side, OSINT can help in:
- Discover bank account owners and other financial transaction-related issues by checking leaked databases
- Monitor public blockchain transactions to track cryptocurrency flow between different wallets
- Collect intelligence from the dark web, such as TOR discussion forums, to discover financial scams, money laundering and how cybercriminals transfer money anonymously
- Search the FinCEN public database to gather different financial information about individuals and companies dealing with the U.S.
- Combine financial information acquired from public databases to corporate records in corporations profiles to reveal true ownerships of companies
- Build a financial profile of the target person/company by correlating financial transactions and asset information from public sources
Identifying secret routes
Tracking transportation companies can help reveal hidden routes used to deliver drugs to key markets worldwide
Geospatial data
Commercial satellite images can reveal drug dealers' camps and farms. Google Maps and Street View can reveal the actual addresses of suspicious persons and companies, whether correct or fake.
Investigating public records
We can investigate many sides related to individuals and organizations involved in drug trading by searching public databases, such as court documents, property records and business registrations.
Future analysis
Law enforcement agencies can use OSINT to discover historical data related to drug trafficking, which allows them to predict future trends and preferred delivery routes by drug dealers.
Identifying and investigating drug dealers on social media with Silo for Research
The first step when conducting an investigation using Silo for Research is to select a regionally appropriate egress location and a user agent string that matches regional norms. This workflow will use a U.S. egress location and Google Chrome running on a Windows 10 machine as the user agent string. This process allows investigators to blend in as locals of that area.
An example of points of presence available to Silo for Research users including geographic locations and the dark web
When conducting research on social media, there are various data capture tools included with Silo for Research that can be used for gathering intelligence. This first is a video download tool; this tool allows investigators to simply download any video currently playing on their screen to save as evidence. The second is a screenshot tool that gives investigators the ability to take a screenshot of an entire page. The screenshot tool also gives investigators the ability to edit the screenshot by including boxes, arrows and text to highlight important information, as well as the ability to include the URL of where the screenshot was taken. This allows investigators to return to that page to gather additional intelligence quickly.
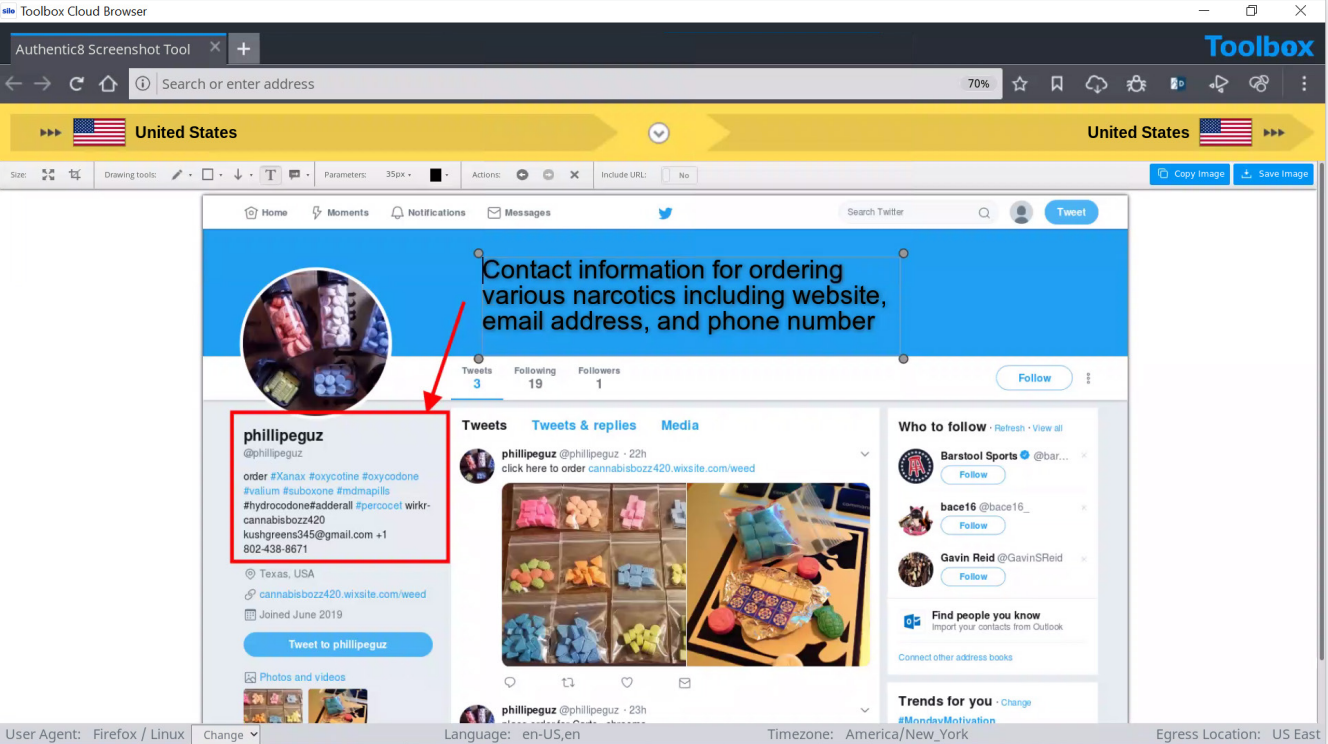
By conducting a search on Twitter for #xanax, the Twitter user @phillipeguz was identified as an account using Twitter to market and sell illegal narcotics. Shown on this profile is information on how to place an order; the information listed includes a website, email address and phone number. This information can now be run through additional search engines to possibly identify the owner of the account.
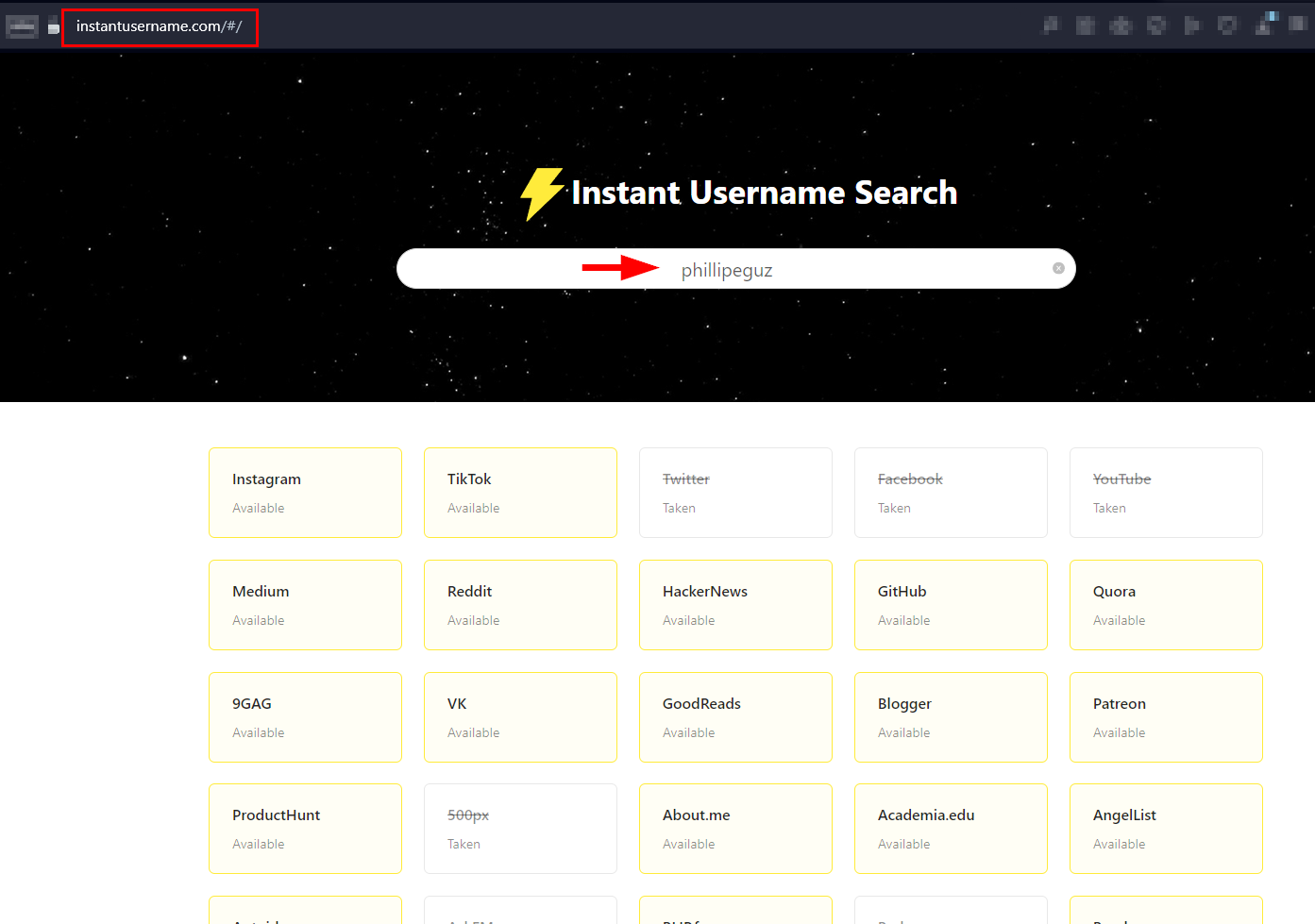
Searching for a particular username across social media networks
Now that we have the target username on Twitter @phillipeguz, we can conduct a reverse username search to find all social media profiles carrying the same username. Instant Username Search is a free online service providing such capability.
Resources for site ownership research
WHOIS Records: WHOIS records provide top level domain information such as exact dates of registration, addresses, names, and phone numbers associated with the domain. Additionally, it provides web host information. @phillipeguz posted the website https://cannabisbozz420.wixsite.com/weed/about on their Twitter feed as a location to purchase the illegal narcotics. Using https://urlscan.io, a report was generated for this site.
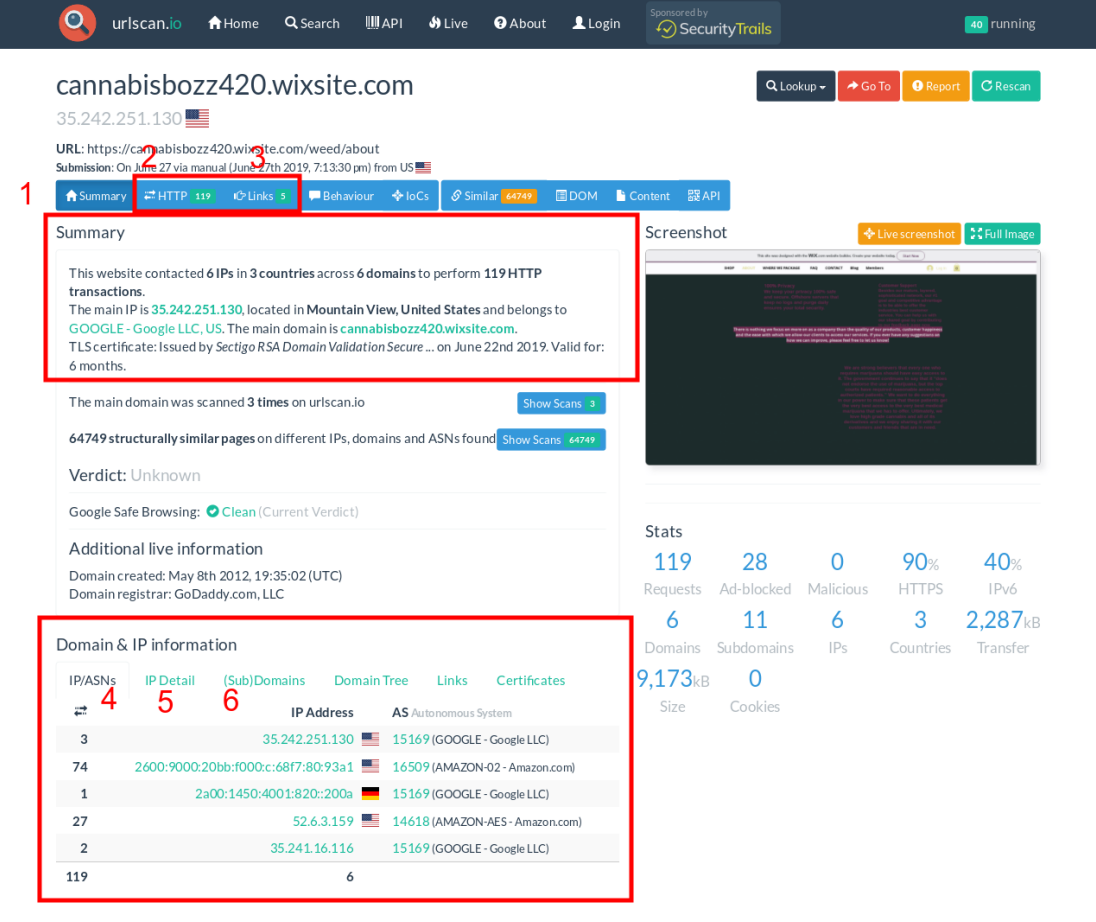
Breakdown of URLscan.io result panels:
- "Summary" provides a top level summary of what country the site is hosted in.
- "HTTP" details how many HTTP connections are made during initial load.
- "Links" details what other sites are linked to on the main page.
- "IP/ASN" details the IPs of everything used upon initial load and the geographic location as well as ASN.
- "IP Detail" contains the exact city/state/country an IP address is assigned to, and redirects.
- "(Sub)domains" identifies how many subdomains a top level domain contains.
Example analysis of result panels:
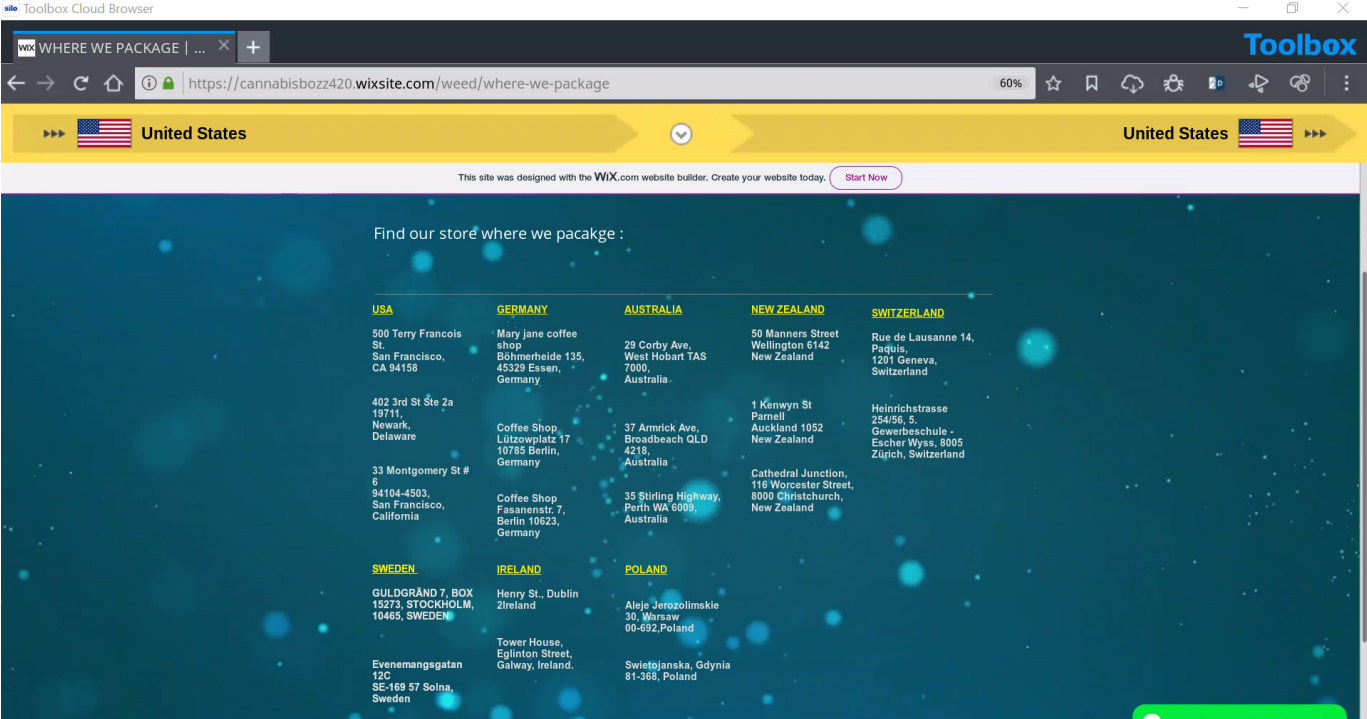
According to the generated report, https://cannabisbozz420.wixsite.com/weed/about uses hosting primarily in the United States but also has hosting in Germany. This means that the distribution could also include locations outside the United States. On the website, the site owners also listed packaging locations in the United States, Germany, Australia, New Zealand, Switzerland, Sweden, Ireland and Poland. The following screenshot from their website depicts their packaging locations around the world. It appears that the domain was registered by godaddy.com. This information could be used to send out a subpoena or court order to godaddy.com to find out who registered the domain with them.
Finding the hosting company
Sometimes, a website's domain name register could differ from the hosting company. We can use a free online service like digital.com to detect the hosting company.
Finding connected websites
Website owners use the Google Analytics service to monitor traffic on their websites. Typically, webmasters use a single analytics account to monitor multiple websites. We can conduct a reverse Google Analytics search to discover all websites using the same ID. Here are two online services for doing this:
Website history
The Wayback Machine is one of the most popular online services for fetching previous versions of websites. Archived versions may contain contact information and identifiers (mail address and information hidden in webpage source code, such as the web designer's name or company) that can assist with attributing ownership. This data found in historical captures can aid open source investigations and analysis.
Phone number reverse lookup
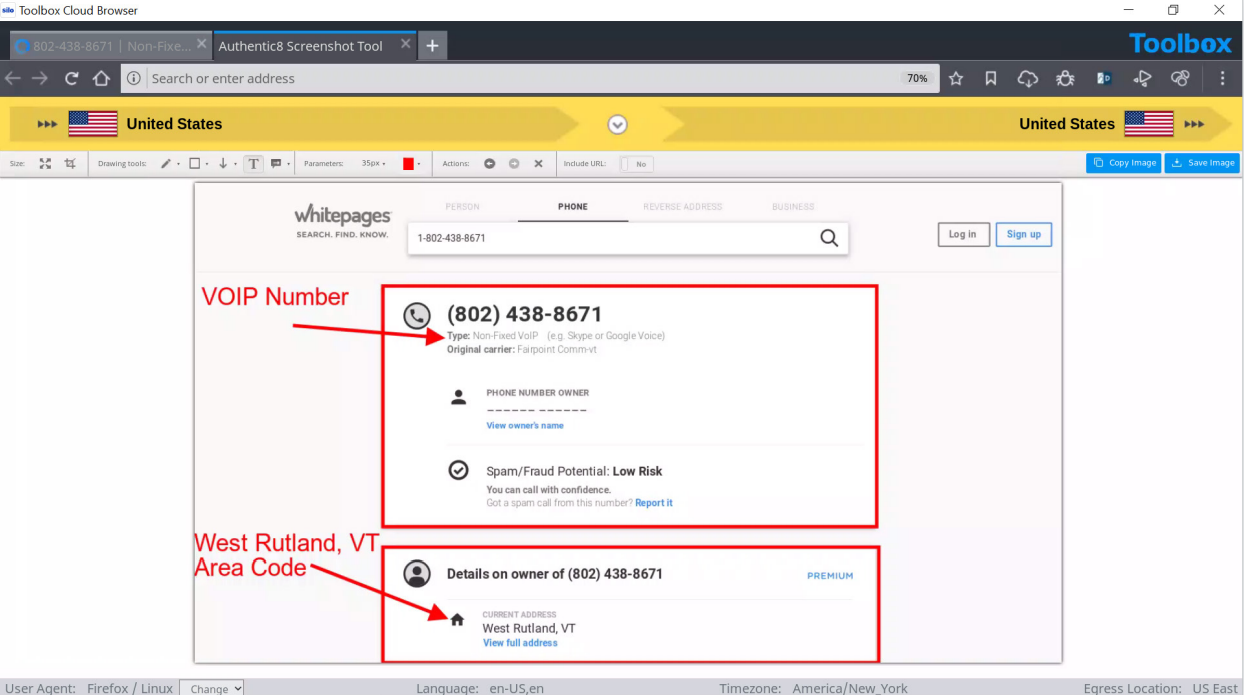
The phone number +1-802-438-8671 was also listed as contact information for ordering narcotics from this Twitter page. Having this number available is extremely valuable for the investigation. The number can be run through a reverse phone number search engine to identify the subscriber information. The following screenshot is from a report generated by https://www.whitepages.com/phone/1-802-438-8671 for the listed phone number.
Example analysis of result panels:
Although there is no identity listed for the number and the number is associated with a voice over internet protocol (VoIP), there is some valuable information that can be pulled from the report. Seeing that the number has a Rutland, Vermont area code is telling: due to the website listing a packaging location on the East Coast, it is possible that the East Coast is their shipping HQ.
Other online services for conducting reverse phone lookups are Truecaller and Spokeo.
Searching for additional social media profiles by email
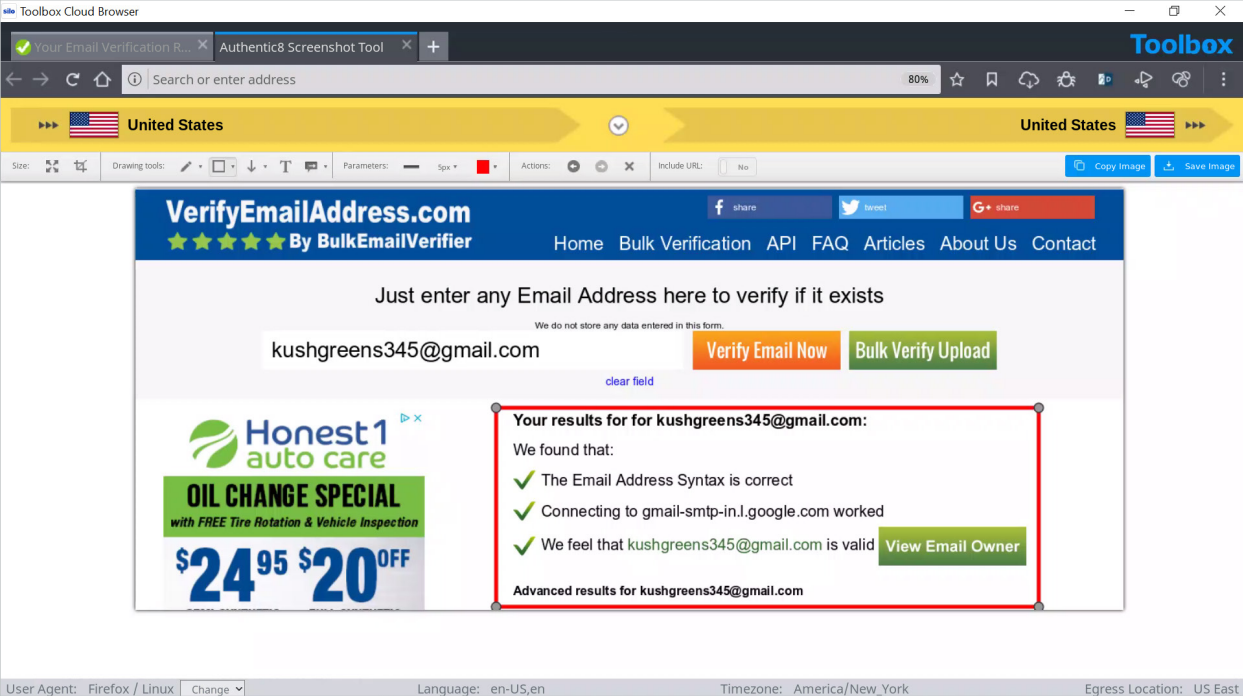
The third piece of contact information listed on this Twitter page is the email address kushgreens345@gmail.com. Once a possible email address is identified for a target, it can be run through https://verifyemailaddress.com to verify that it is a legitimate email address. Once an email address is verified, a subpoena or court order can be sent to the email provider to identify who owns and operates that email address. The screenshot below depicts the results from https://verifyemailaddress.com for the email address kushgreens345@gmail.com, and it is in fact a legitimate email address.
We can also conduct a Google search to find all locations where this email appears.
“kushgreens345@gmail.com”
Search for previous data breaches
A subject's email address can be searched on data breach notification services like HaveIBeenPwned and BreachDirectory to identify online accounts associated with that address that have been compromised in past breaches.
With drug dealers increasingly utilizing social media to distribute illegal narcotics, investigators need a safe and anonymous method to investigate and capture social media data. This workflow covered how Silo for Research can be used by investigators to safely and anonymously investigate and capture data from social media drug dealers.
To learn more, visit our website or request a demo of Silo for Research.
Tags Law enforcement OSINT research Social media
